In a previous blog post, I configured pxGrid integration with StealthWatch and ISE using a CA-Signed certificate. In this blog post, I'm going to go through the configuration using self-signed certificates to enable StealthWatch to mitigate threats on the network using ISE.
To ensure that this will work with ISE, the following should be configured before we start:
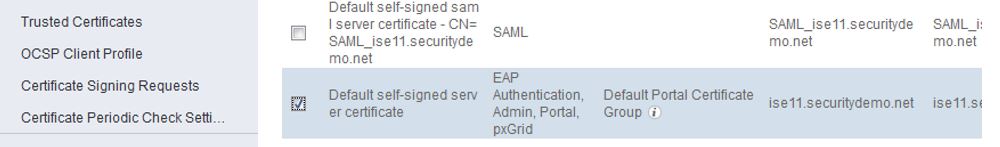
- Navigate to Administration>System>Certificates>System Certificates and ensure the default self-signed certificate in ISE is used for pxGrid:
- Navigate to Administration>System>Deployment>ISE-Node and make sure that the pxGrid Persona is enabled
- Make sure that the ISE node will automatically approve new accounts by navigating to Administration>pxGrid Services>Settings (or in ISE 2.0 and below, just navigate to Administration>pxGrid Services and click Enable Auto-Registration on the top)
After that is done, navigate to Administration>System>Certificates>System Certificates and check the box next to the self-signed certificate. Click Export.
When exporting the certificate, choose the radio button for Export Certificate Only and click Export.
Open up the StealthWatch Management Center in your browser and click on Admin User>Administer Appliance. Then navigate to Configuration>Certificate Authority Certificates. On this screen, you will upload the ISE self-signed certificate to the trusted CA certificate store as shown below:
Navigate to Configuration>Services and enable SSH access to your StealthWatch Management Center as root. After you have done that, use Putty to SSH to your StealthWatch Management Center and issue the following:
openssl genrsa -des3 -out selfsmc.key 2048
As it's issuing this key, it'll ask you to enter a passphrase. I just ended ISEc0ld since it would be easy for me to remember.
After the key is issued, we're going to create a certificate signing request by issuing the following:
openssl req -new -key selfsmc.key -out selfsmc.csr
It'll ask for the passphrase for the key (ISEc0ld) and then have you enter some basic parameters for the CSR. One thing to note: At the end, it asks for an optional challenge password if you would like to use one. I chose to keep this blank since it's optional
Next we will create the self-signed SMC certificate by issuing the following:
openssl x509 -req -days 365 -in selfsmc.csr -signkey selfsmc.key -out selfsmc.cert
It will ask you again for the passphrase of the key (ISEc0ld)
Next I will decrypt the key with the following:
cp selfsmc.key selfsmc.key.org
openssl rsa -in selfsmc.key.org -out selfsmc.key
It'll again ask for the key passphrase (ISEc0ld)
After you have finished, use WinSCP to connect to your StealthWatch Management Center via SCP and copy the files you just created to your local disk:
In your browser, navigate back to the StealthWatch Management Center if you aren't there already. Then click on Admin User>Administer Appliance and then navigate to Configuration>SSL Certificate
Scroll down to the SSL Identity Certificates field and upload the self-signed .crt file you just created in the Target Certificate File field and upload the key file in the Private Key field.
In ISE, navigate to Administration>System>Certificates>Trusted Certificates and click Import:
Upload the SMC .crt file we just created and make sure that it will be trusted for authentication:
In the StealthWatch Management Center, go back to the dashboard and then navigate to Deploy>Cisco ISE Configuration (if using 6.8) or Tools>Cisco ISE Configuration (if using 6.7):
Fill out the following information:
- Cluster name - Can be the name of your ISE server or whatever else
- SMC Syslog port - 3514 is the default. This is the port ISE will send over logs from
- ISE username and password
- Primary ISE node and IP address
Click Save when done
You should get the following pop-up if the connection is successful:
If all is configured correctly, you should have a green circle showing that your communication with ISE is established and an Add Cisco ISE Mitigation button. Click on that button.
On the Cisco ISE Mitigation screen, pick the SMC self-signed identity certificate from the drop-down and then add the name and IP address of the ISE Primary Admin node and (optionally) the secondary PAN node. Click Save when complete.
The following pop-up should come up:
In ISE, navigate to Operations>Adaptive Network Control>Policy List and click Add. We will create an ANC policy here:
Since we're going to be using ISE and StealthWatch for Quarantine, name your ANC policy Quarantine and the action that should be taken is Quarantine. Click Submit.
Navigate to your Policy in ISE and there should be a Exceptions rule under your Authorization policy. Create the following exception rule:
Name: ANC - Conditons: Session:EPSStatus EQUALS Quarantine Then: DenyAccess (or whatever result you want your quarantined endpoints to have)
Note: If you are using Policy Sets, your Global Exceptions policy will be on the left-hand side under Policy>Policy Sets:
Navigate to Administration>pxGrid Services>Clients and you should now see your SMC under clients. Check the box next to the SMC client and click the Group button:
Remove the Basic group and add the EPS group. Click Save
Your SMC client now is a part of the Endpoint Protection Services group as you can see below:
Next we will configure the logging. Navigate to Administration>System>Logging>Remote Logging Targets and click Add:
Name the remote target something to do with StealthWatch so you can easily identify it. Make sure that the IP address is the SMC and the port is 3514 since that's what we configured over in StealthWatch. Click Submit when finished.
Then navigate to Administration>System>Logging>Logging Categories and add the remote logging target to the following categories:
- Passed Authentications
- RADIUS Accounting
- Administrative and Operational Audit
- Proflier
Now you are done with your configuration. You should be able to quarantine and unquarantine from StealthWatch through ISE. If you go back to StealthWatch and navigate to Monitor>Hosts and pull up a host, you should see the Quarantine and Unquarantine buttons for that host: